In context: Google’s search ads are already deceptive enough. Sure, they are marked with a “sponsored” indicator, but they still appear as a legit search result that could trick the inattentive into clicking an ad when they only wanted information. What makes matters worse is that bad actors have figured out multiple ways to abuse these faux search results to scam people.
A common tactic for getting people to download and install malware is to trick them into clicking a search ad disguised as the legit company that makes the desired software. Malwarebytes reports that attackers now use Punycode in Google Ads to make their URLs look even more authentic.
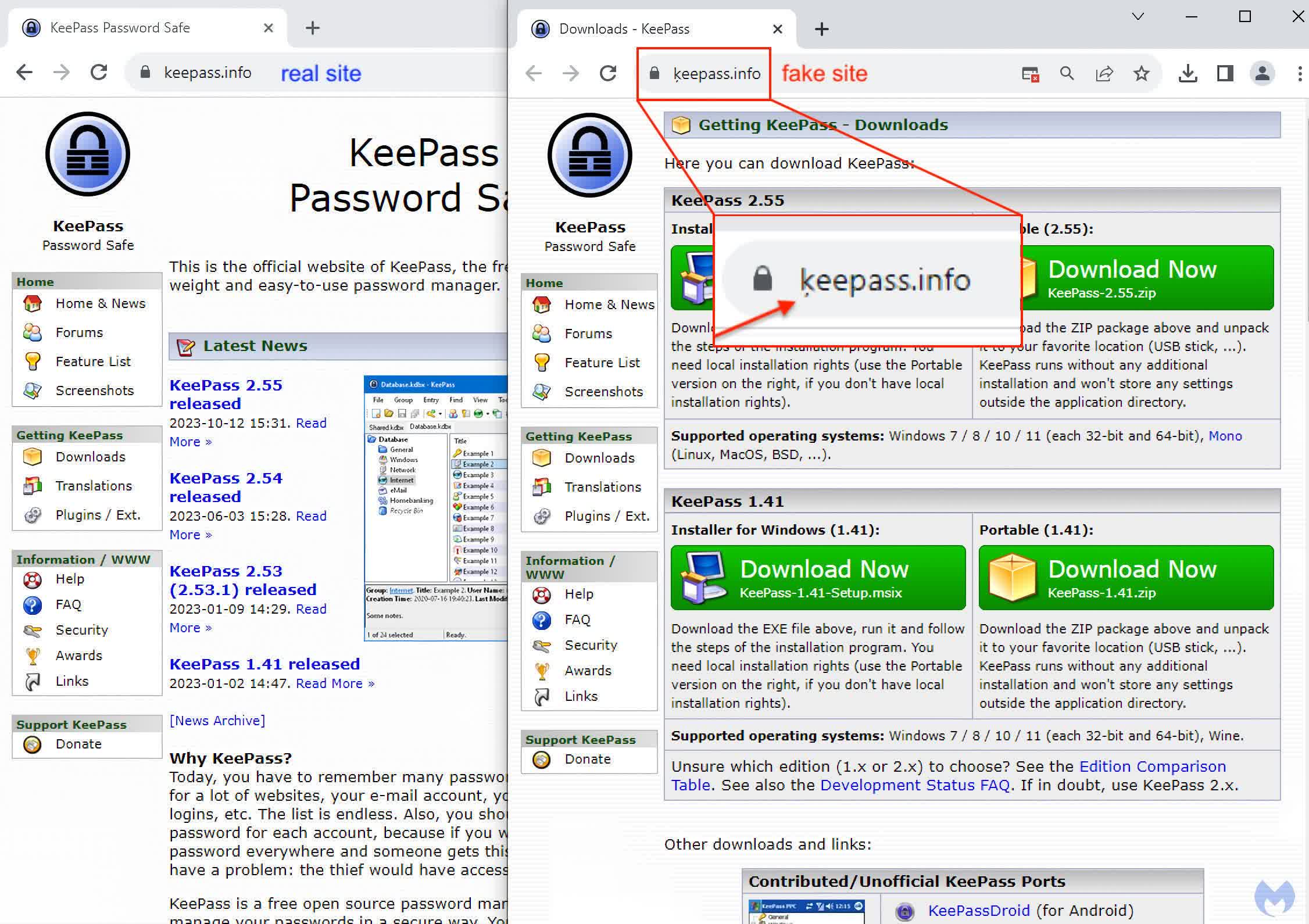
This tactic is called a “homograph attack” because it uses Unicode characters of non-Latin scripts, like Cyrillic, Arabic, Greek, Chinese, and others, to create a cloned URL that leads to a scam website. Malwarebytes points to a recently found malicious Google ad for the KeePass password manager as an example.
Previously, attackers would use subdomains and extensions similar to the site they were mimicking to trick users into clicking, but these are pretty easy to spot. However, by translating a URL into Punycode, bad actors can create an address that looks completely authentic.
As you can see in the image above, the bogus URL looks identical to the authentic one below it. This trick is sneaky enough to fool the most attentive and tech-savvy users. The only giveaway appears after clicking the bogus ad and going to the malicious website. Once there, the browser’s address bar will show the address in Unicode, giving the ruse away. Unfortunately, unless the user knows it could be a scam, most won’t even look at the address bar, especially when the website that appears is nearly identical to the software company’s.
However, even looking at the Unicode address in the browser, users could still miss the subtle visual cue if they aren’t looking carefully. Notice in the image below how the only difference between the legit address on the left and the bogus one on the right is the tiny symbol under the ‘k.’ Users could easily miss this sign or dismiss it as a speck on their monitor.
Homograph attacks have been around for a while, but this is the first time Malwarebytes has seen it used in conjunction with Google ads. Unfortunately, there’s no simple fix, especially if attackers use other techniques to make their fake sites seem real.
Your best bet is to avoid clicking search result ads when looking for software. It’s best to go directly to the company’s website and look for the software straight from the source or use a trusted mirror like TechSpot Downloads. We authenticate all our downloads, scanning the software locally and through VirusTotal to ensure they are malware-free.
Bottom line: Avoid clicking ads in Google search results. We have issued similar warnings that they can’t be trusted. At the least, you are handing Google your ad preferences to add to your existing (and likely extensive) advertising profile. At worst, you could land on a website that means to do you harm. Until Google figures out a way to prevent bad actors from abusing its ad platform, there is really no legitimate reason to click on their ads.

